Consensus algorithm
Transformers chain is a completely decentralized public chain that utilizes the independently developed Raindrop Protocol to solve various shortcomings of traditional consensus mechanisms.
POW requires a large amount of energy to solve mathematical problems, which can lead to energy and resource waste. Miners with stronger computing power have a higher probability of success, which may lead to the concentration of computing power in several large mining pools, thereby increasing the risk of centralization.
POS requires holding a certain number of tokens, and those with more tokens also have a higher probability of success, which may lead to wealth inequality and centralization risks.
The Raindrop Protocol solves the problems of energy waste, resource waste, and suspicion of centralization while ensuring safety.
Concept of Consensus Mechanism
Digital currency and blockchain complement are complementary to each other. Blockchain, as the underlying technology of digital currencies, relies on consensus mechanisms.As an Internet-based decentralized accounting system,without strong centralized role control all nodes participating in the blockchain need to reach a consensus and establish mutual trust relationships.
Raindrop Protocol
Transformers uses Raindrop Protocol as consensus mechanism at the consensus layer. At present, the mainstream consensus mechanism cannot balance efficiency and decentralization. Compared with traditional POW, Raindrop Protocol is more efficient and will not generate competition for computing power. Each node in the network has its own unique node ID , and each node in the main network is selected and verified through discrete random numbers.
VRF validates the random number selection of block packers, ensuring the fairness and transparency of the election process. The entire network nodes verify whether the verification nodes selected by the block packers are randomly selected through VRF.
The use of VRF (Verifiable Random Function) has the following characteristics:
- Fairness and Transparency: Random numbers generated through VRF have fairness and transparency, and anyone can verify the correctness and authenticity of random numbers.
- Unpredictability and unforgeability: Due to the unpredictability and unforgeability of the VRF generation algorithm, the generated random numbers have high security and trust.
- Cost saving: Using VRF can avoid the additional overhead and risks that may exist in traditional random number generation methods, thereby effectively saving costs.
Raindrop Protocol features
-
Security: Raindrop Protocol prevents issues such as dual payment and
51%attacks, and has the ability to protect the network from attacks and malicious behavior while ensuring decentralization and distribution. -
Scalability: As the number of system users and transaction volume increases, the Raindrop Protocol can support higher throughput and more participants, without compromising security during the expansion process.
-
Fairness: Raindrop Protocol adopts discrete random numbers to ensure that every participant has an equal chance of receiving rewards and encourages nodes to comply with rules.
-
Verifiability: Anyone can use verifiable random numbers to verify whether a new block is legal and whether the transactions within it are valid.
-
Economic efficiency: Raindrop Protocol does not require a large amount of computing power to calculate. Due to the low energy consumption of nodes, it saves more energy and resources. This can improve the economic efficiency of the entire system, allowing more nodes to participate in the system and receive corresponding rewards.
Algorithm &Security
In order to protect the security of assets on the chain, Transformers has adopted algorithms and security mechanisms that are currently widely used and tested through extensive practice. It mainly includes two aspects: the ED25519 elliptic curve signature algorithm and the Verifiable Random Function (VRF).
ED25519 elliptic curve has been widely recognized for its security from both mathematical and practical perspectives.It also has extremely fast generation and verification speeds, and improves the verification speed of transactions while ensuring security. For more information about ED25519 elliptic curve, please refer to relevant literature:http://ed25519.cr.yp.to/
Transformers chain uses a large number of random number algorithms to ensure its fairness in the transaction process. However, ordinary random number algorithms cannot prevent the malicious behavior generated by modifying the source code. So the transformers chain introduces VRF to verify the randomness of the results. The related principles can also be found in relevant documents. Verifiable random function - Wikipedia
Consensus process
Node Role
There are four types of node roles in the transformers network. Node roles are just the roles that a node plays in a certain transaction process, not an identity. That is:
Initiating node: the node that initiates the transaction. Organize the transaction and send it to the packaging node.
Packing node (delegate node): the node responsible for the flow of the initiated transaction and packaging the transaction into blocks. After the transaction is packaged into a block, it sends the blocks to the verification nodes. and the block will be broadcast to the entire network after the verification.
Verification node (candidate delegate node): the node that verifies the blocks sent by the packaging node. If the verification is successful, it notifies the packing node.
Other nodes: nodes that do not participate in the transaction process. These nodes only verify the broadcast blocks and store them in the database.
In transformers chain, each node may play any of the above four roles, and in fast transactions, a node may play four roles simultaneously.
Transaction process
During the entire transaction process, it is necessary to select several nodes within the entire network. All selection processes follow the principle of fairness and randomness, using VRF for selection and validation.
The process is as follows:
- The initiating node uses VRF to select the packing node based on the data block information and sends the transaction to the packing node.
- The packing node verifies the VRF to ensure that it is the node selected by the initiating node and selects several nodes among the network nodes to send the transaction to.
- The receiving nodes verify the transaction and VRF. If the verification is successful, they notify the packing node.
- When the number of notifications received by the packing node reaches the consensus number, it puts the transaction in the cache. The packing node packs all transactions in the cache into blocks at a specific time interval.
- The packaging node uses VRF to select several nodes from the block as the validation node and send the block to the validation node.
- The verification node verifies the block and VRF. If the verification is successful, they notify the packing node.
- When the number of notifications received by the packing node reaches the consensus number, it is broadcasted to the entire network.
- After receiving the broadcast, other nodes perform VRF verification to determine that the packing node ( i.e.,the broadcast initiator)is the packing node specified by the initiating node.
Advantages:
The mainstream consensus mechanisms in blockchain include Proof of Work (POW) mechanism and Proof of Stake (POS) mechanism, while transformers adopts the independently developed Raindrop Protocol, which has the following advantages:
- Stability:
The POS mechanism may cause fluctuations in token prices and have a significant impact on the network. Because POS requires staking tokens to participate in consensus, and a decrease in token prices may cause users willing to participate in consensus to exit, thereby affecting the stability of the network.
With the increase of transaction volume, the load of the POW network will become very heavy, leading to slower transaction speed, and this problem cannot be simply solved by expanding block size or increasing transaction costs.
In Raindrop Protocol, the selection of packaging nodes is based on qualified nodes and does not involve staking tokens to participate in consensus. As the network size continues to increase, Raindrop Protocol does not require too much computing power, so it will not affect transaction speed
- Fairness:
In the POS mechanism, those who holding more tokens are more likely to receive block rewards and transaction fees, which can exacerbate wealth inequality and lead to network centralization. The fairness of the initial allocation of tokens is also very important, as it will affect the wealth distribution of the entire network. If there are issues with the initial allocation of tokens, it will lead to an unfair situation in the network.
In the POW mechanism, miners with higher computational power are more likely to receive block rewards, which leads to centralization of computational power. Oligopoly may affect the fairness and security of the network.
In Raindrop Protocol, the packaging nodes are randomly selected through VRF verifiable random numbers, and it is not a winner take all problem.
- High efficiency:
Using the POW mechanism can achieve one packet and one block in ten minutes, and using the POS mechanism can achieve one packet and one block in fifteen seconds. In transformers chain, using the Raindrop Protocol can achieve the fastest speed-chaining up in one second.
Hash function
A hash function, also known as a hash algorithm, is not used to complete data encryption and decryption, but is an important technology used to verify data integrity.
Through the hash function, a "digital fingerprint" (hash value, digital digest) can be created for the data. The hash value is usually a short string of random letters and numbers. Both the sender and receiver agree on the specific hash algorithm before communication, and the algorithm is publicly available. If the message is tampered with during transmission, the message cannot match the obtained digital fingerprint.
Hash functions are widely used in the verification of data integrity and are the core technology of digital signatures. Common algorithms include MD (message digest algorithm), SHA (message hash algorithm), and MAC (message authentication code algorithm). Transformers uses the SHA256 algorithm to ensure speed and security.
Digital Signature
Basic characteristics of digital signature: authenticity, non-repudiation,integrity.
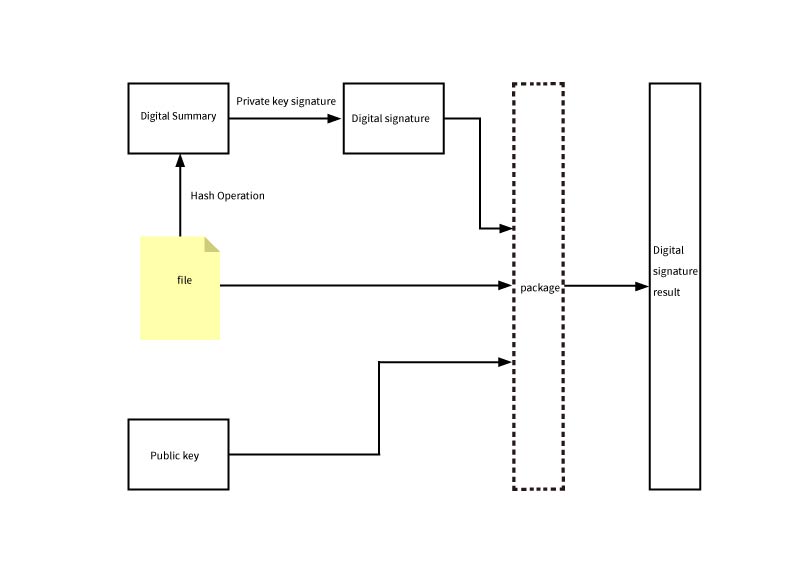
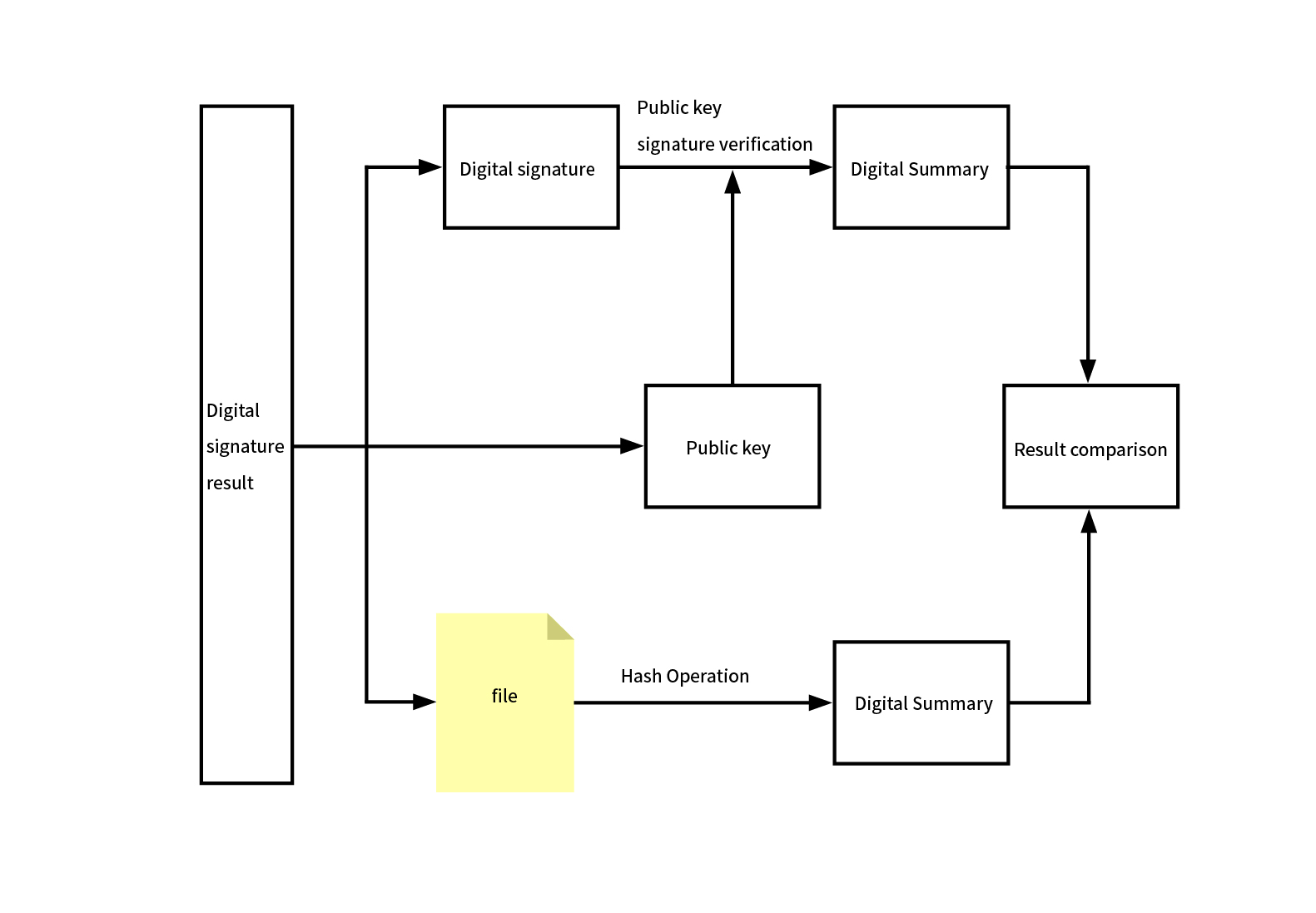
Digital signature (also known as public key digital signature or electronic signature) is a method for authenticating digital information, similar to a physical signature written on paper, but implemented using techniques from the field of public key encryption. .A set of digital signatures typically defines two complementary operations, one for signing and the another for verification.A digital signature is a digital string that can only be generated by the sender of the information and can not be forged by others. This string of numbers also serves as valid proof of the authenticity of the information sent by the sender..Digital signature is the application of asymmetric key encryption technology and digital digest technology.Digital signing is an encryption process, while digital signature verification is a decryption process.
Transformers adopts digital signature because it ensures the non-repudiation of the message ,as others cannot forge the sender's private key signature. The sender encrypts the information with its own private key,which can only be decrypted using the sender's public key. It can ensure the integrity of the message. A digital signature uses a specific hash function, and the resulting digital digest values for different files are also different.
The Raindrop Protocol used by transformers employs a discrete random number algorithm to randomly select verification nodes from the verification pool for multi-linear broadcast data verification. The legitimacy of a block is determined by the final signature verification that satisfies the protocol.
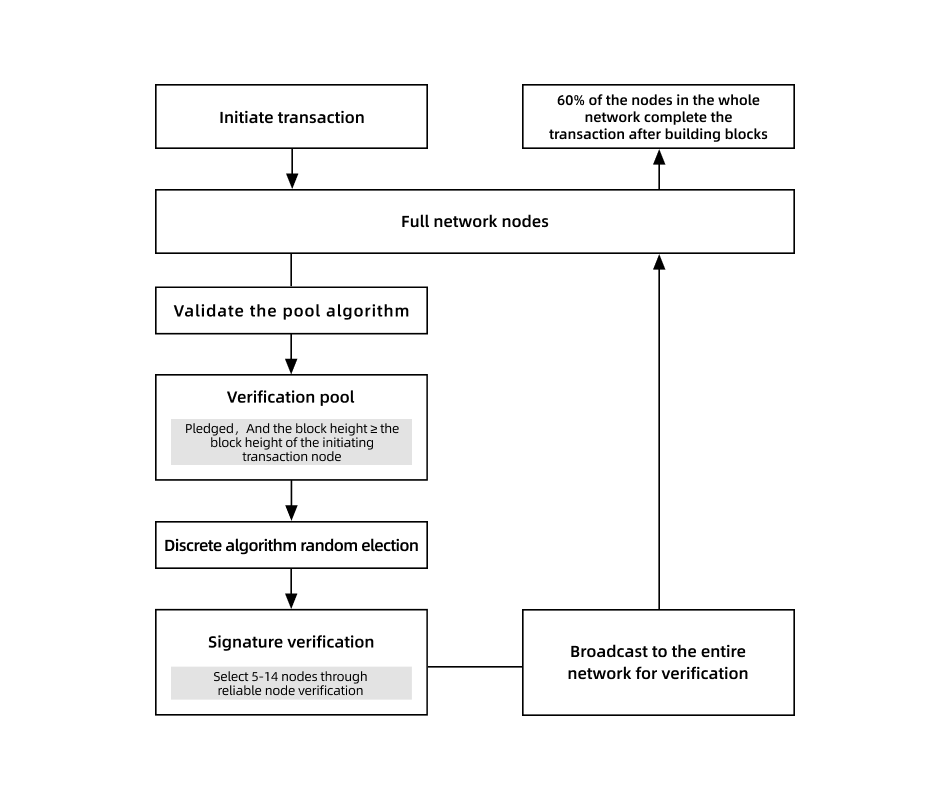
The Raindrop Protocol avoids the centralization of computing power and the "winner-takes-all" problem brought by the free competition for accounting rights in traditional Proof of Work (POW), achieving a balance between fairness and competitiveness to a certain extent. In the transformers network, higher throughput can be achieved with the continuous increase of validation nodes. When the number of nodes reaches a certain scale, the low-power operation of the nodes and the increasing availability of validation nodes in the future will greatly control the transaction costs. The Raindrop Protocol executes computations through CPUs, resulting in significantly reduced costs compared to GPUs, ASICs, and other alternatives.
Consensus process
On-Chain Confirmation
In traditional blockchains, the slow block generation speed and block size limitation result in slow on-chain confirmation speed. However, on transformers chain, an unlimited number of transactions can exist in a single block while ensuring data security and decentralization.
The on-chain confirmation speed of transformers can reach as fast as 0.1 seconds with a network-wide acceptance rate set to 75%.
This value is the optimal ratio of speed and success rate after verification and practice. If the broadcast does not reach the acceptance threshold set by the network, nodes with updated data status will validate and roll back those failed transactions in the synchronization mechanism.